Are you truly in control of your IoT devices, or are they silently vulnerable to unseen threats? Remote IoT device login via IoT Core is not merely a convenience; it's the linchpin of modern, secure, and efficient IoT ecosystems. This capability allows for seamless management and monitoring, but demands a robust understanding of its intricacies and potential pitfalls.
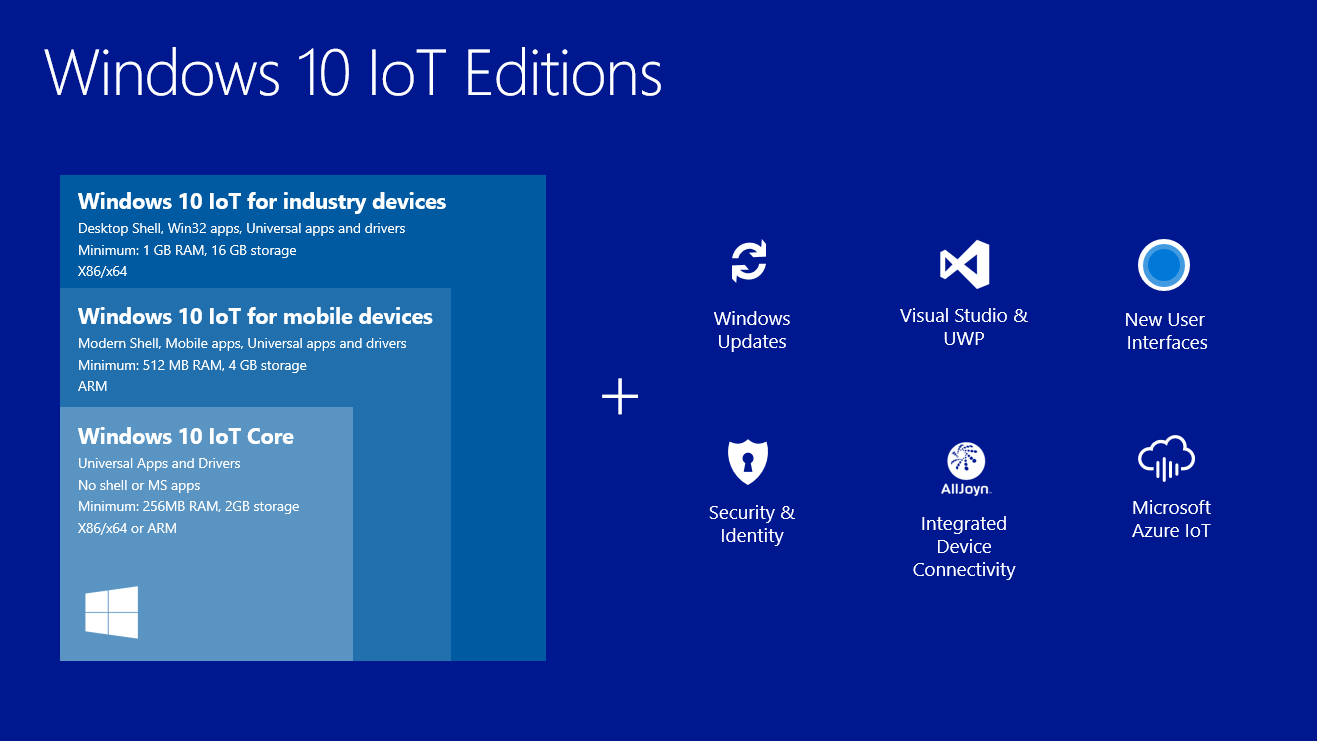
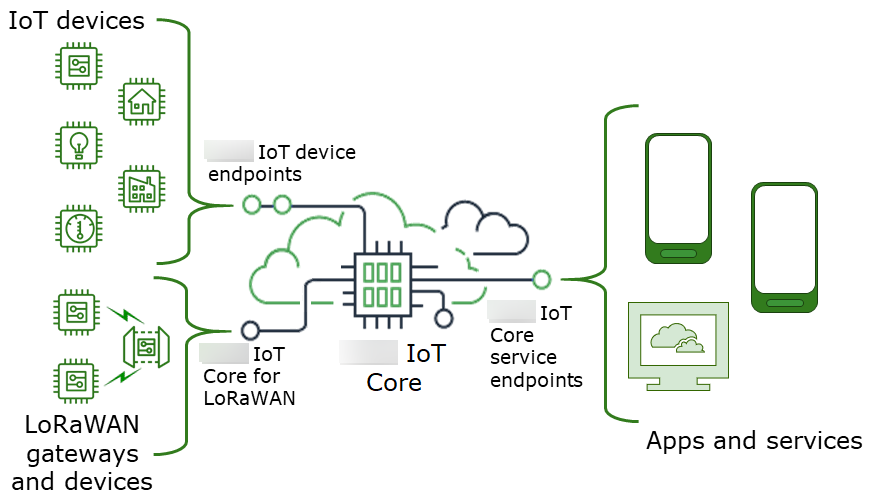
The Internet of Things (IoT) has exploded, connecting devices from smart thermostats to industrial sensors. This interconnectedness offers unprecedented opportunities for automation, data collection, and remote control. However, the ability to remotely access and manage these devices, particularly through IoT Core platforms, has become absolutely critical for businesses and individuals alike. The core challenge lies in establishing secure and reliable remote access to these devices, which are often deployed in environments with limited or no direct human oversight.
| Topic | Remote IoT Device Login & IoT Core |
| Description | Essential for secure and efficient management of IoT devices, enabling remote access, monitoring, and control. |
| Key Technologies | IoT Core platforms (AWS IoT Core, Azure IoT Hub, etc.), MQTT, SSH tunneling, device SDKs (AWS IoT Device SDK), device provisioning services. |
| Security Risks | Unauthorized access, data breaches, malware injection, denial-of-service attacks due to weak security practices. |
| Best Practices | Least privilege access, strong authentication, encryption, regular security audits, secure boot processes, and over-the-air (OTA) updates. |
| Applications | Remote monitoring, predictive maintenance, smart home automation, industrial control systems, smart city initiatives. |
| Reference | AWS IoT Core Official Website |
- Alyx Star Biography Age Net Worth More Revealed
- Aagmaal Gives Join The Movement For Good Share Thoughts